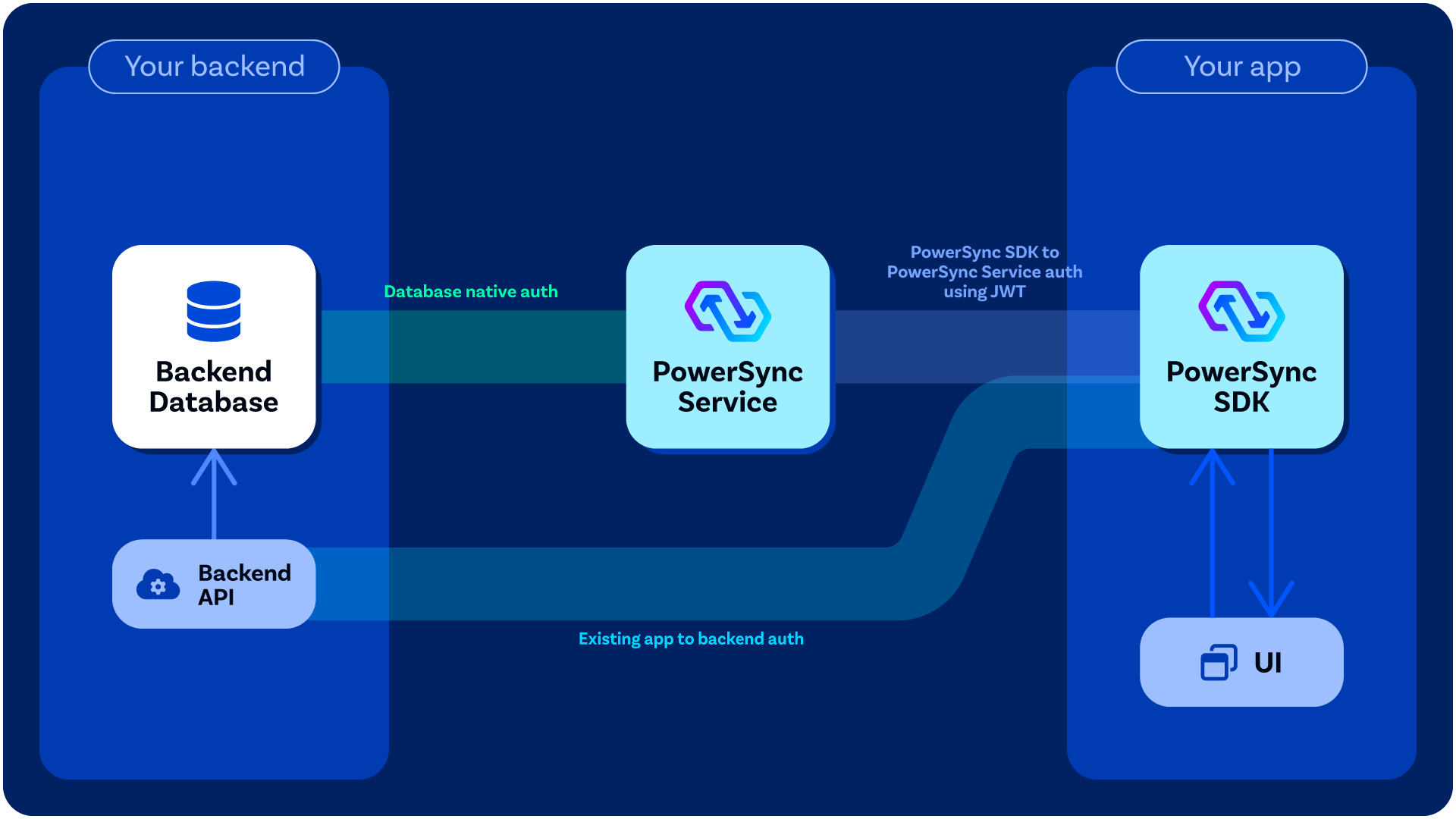
Client Authentication
PowerSync clients (i.e. apps used by your users that embed the PowerSync Client SDK) authenticate against the server-side PowerSync Service using JWTs (signed tokens).
When you call connect() on the client-side PowerSync database, you pass a backend connector as an argument to it, in which you define a fetchCredentials() function that must return a JWT as well the endpoint URL for the PowerSync Service instance that the client will connect to. See here for example implementations. Your fetchCredentials() function will automatically be called by the PowerSync Client SDK whenever it needs it needs a fresh JWT.
Client Authentication Options
Development & Testing
For a quick way to get up and running during development, you can generate Development Tokens directly from the PowerSync Dashboard (PowerSync Cloud) or locally with a self-hosted setup.
Proper Authentication Integration (Needed for Production)
Use Existing JWT from Auth Provider: Some authentication providers already generate JWTs for users which PowerSync can verify directly — see Common Authentication Providers below. In this scenario, your fetchCredentials() function can return the existing JWT from your client-side state.
Custom Auth Integration: Generate JWTs: For others, some backend code must be added to your application backend to generate the JWTs needed for PowerSync — see Custom Authentication. In this scenario, your fetchCredentials() function should make an API call to your backend application to obtain a JWT.
Common Authentication Providers
PowerSync supports JWT-based authentication from various providers. The table below shows commonly used authentication providers, their JWKS URLs, and any specific configuration requirements.
Scroll the table horizontally.
| Provider | Configuration Notes | Documentation | JWKS URL |
|---|
| Supabase | Uses Supabase’s JWT Secret | Supabase Auth Setup | Direct integration available |
| Firebase Auth / GCP Identity Platform | JWT Audience: Firebase project ID | Firebase Auth Setup | https://www.googleapis.com/service_accounts/v1/jwk/securetoken@system.gserviceaccount.com |
| Auth0 | JWT Audience: PowerSync instance URL | Auth0 Setup | https://{auth0-domain}/.well-known/jwks.json |
| Clerk | Additional configuration may be required | Clerk Documentation | https://{yourClerkDomain}/.well-known/jwks.json |
| Stytch | Additional configuration may be required | Stytch Documentation | https://{live_or_test}.stytch.com/v1/sessions/jwks/{project-id} |
| Keycloak | Additional configuration may be required | Keycloak Documentation | https://{your-keycloak-domain}/auth/realms/{realm-name}/protocol/openid-connect/certs |
| Amazon Cognito | Additional configuration may be required | Cognito Documentation | https://cognito-idp.{region}.amazonaws.com/{userPoolId}/.well-known/jwks.json |
| Azure AD | Additional configuration may be required | Azure AD Documentation | https://login.microsoftonline.com/{tenantId}/discovery/v2.0/keys |
| Google Identity | Additional configuration may be required | Google Identity Documentation | https://www.googleapis.com/oauth2/v3/certs |
| SuperTokens | Additional configuration may be required | SuperTokens Documentation | https://{YOUR_SUPER_TOKENS_CORE_CONNECTION_URI}/.well-known/jwks.json |
| WorkOS | Additional configuration may be required | WorkOS Documentation | https://api.workos.com/sso/jwks/{YOUR_CLIENT_ID} |
| Custom JWT | See custom auth requirements | Custom Auth Setup | Your own JWKS endpoint |