The below instructions are currently written for PowerSync Cloud. For self-hosted PowerSync instances, specify database connection details in the config file as documented here.
Postgres Provider Specifics
Select your Postgres hosting provider for steps to connect your newly-created PowerSync instance to your Postgres database:Supabase
Supabase
-
From your Supabase Dashboard, select Connect in the top navigation bar (or follow this link):
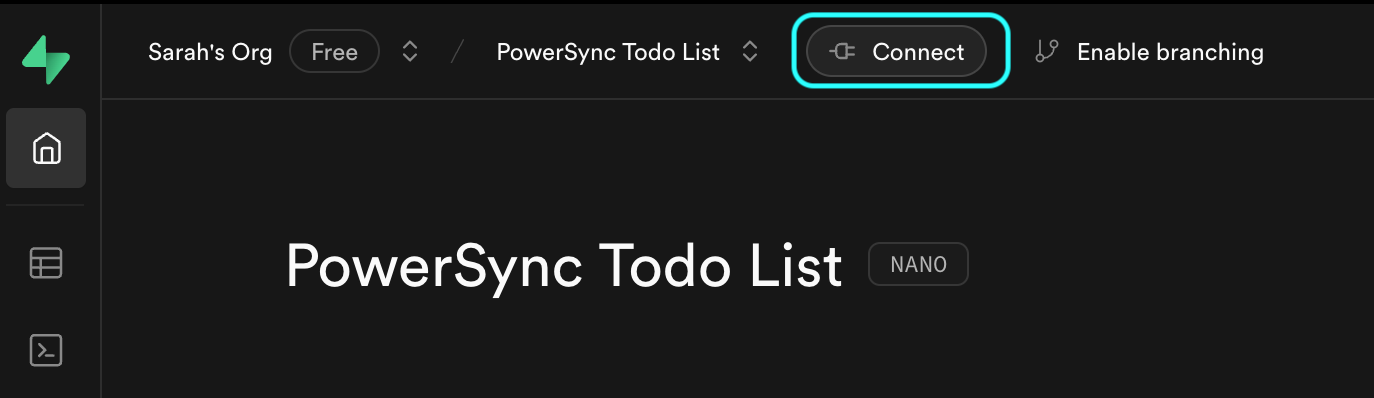
-
In the Direct connection section, copy the complete connection string (including the
[YOUR-PASSWORD]placeholder):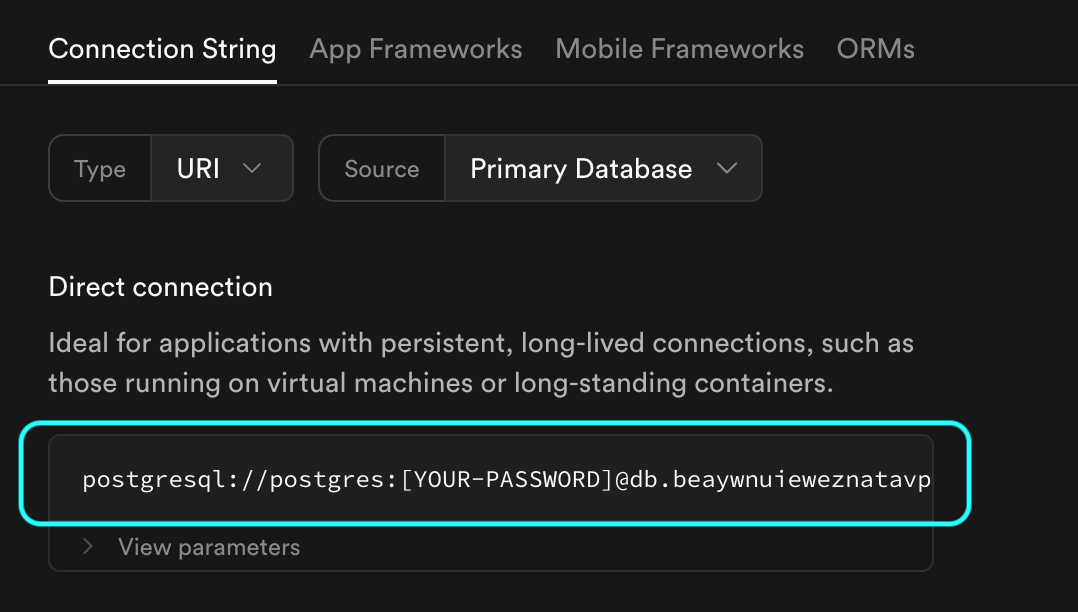
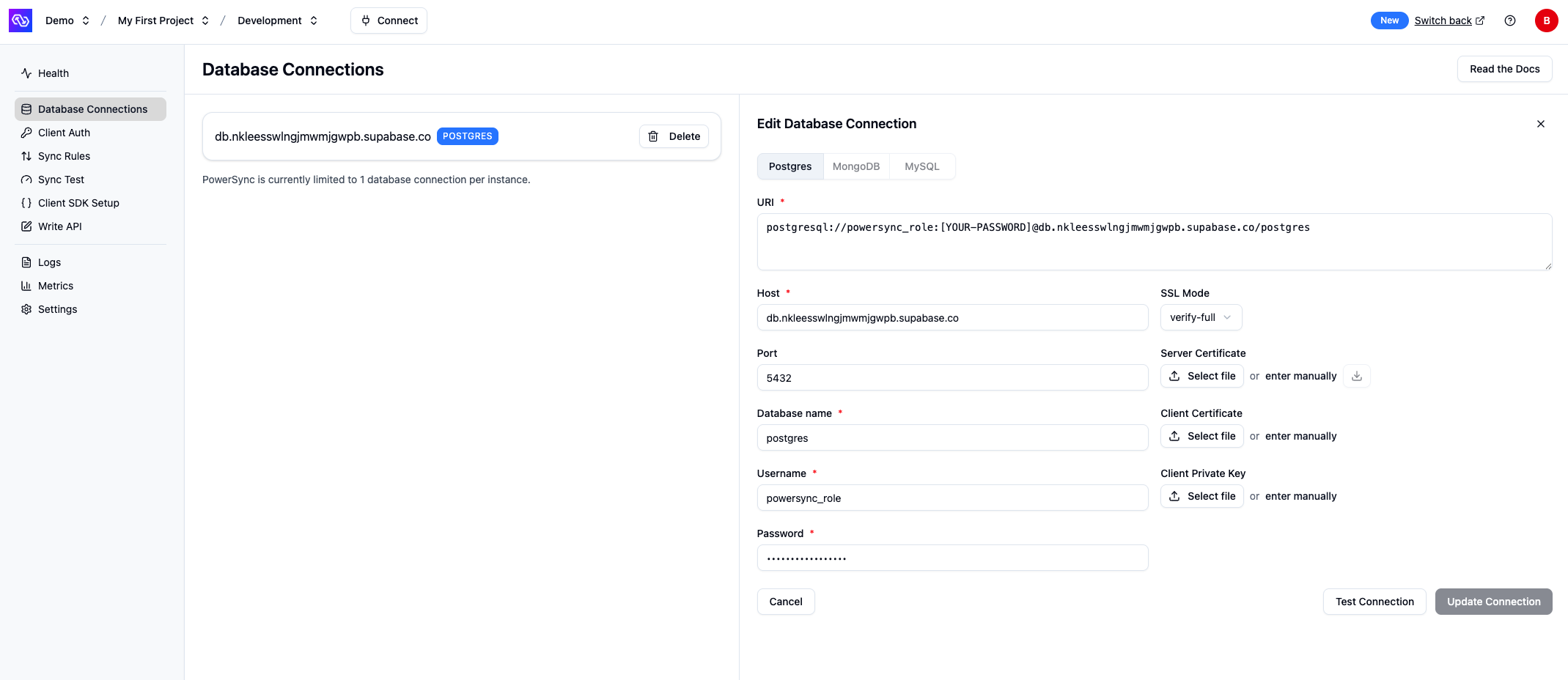
- In the PowerSync Dashboard, select your project and instance and go to Database Connections.
- Click Connect to Source Database and ensure the Postgres tab is selected.
- Paste the connection string into the URI field. PowerSync will automatically parse this URI to populate the database connection details.
-
Update the Username and Password fields to use the
powersync_roleand password you created when configuring your Supabase for PowerSync (see Source Database Setup). -
Note: PowerSync includes Supabase’s CA certificate by default, so you can use
verify-fullSSL mode without additional configuration.
- Verify your setup by clicking Test Connection and resolve any errors.
- Click Save Connection.
Enable Supabase Auth
After your database connection is configured, enable Supabase Auth:- In the PowerSync Dashboard, go to Client Auth for your instance.
- Enable the Use Supabase Auth checkbox.
- If your Supabase project uses the legacy JWT signing keys, copy your JWT Secret from your Supabase project’s settings (JWT Keys) and paste the secret into the Supabase JWT Secret (optional) Legacy field in the PowerSync Dashboard. If you’re using Supabase’s new JWT signing keys, you can leave this field empty (PowerSync will auto-configure the JWKS endpoint for your project).
- Click Save and Deploy to apply the changes.
Troubleshooting
Supabase is configured with a maximum of 4 logical replication slots, with one often used for Supabase Realtime (unrelated to PowerSync).It is therefore easy to run out of replication slots, resulting in an error such as “All replication slots are in use” when deploying. To resolve this, delete inactive replication slots by running this query:AWS RDS
AWS RDS
- In the PowerSync Dashboard, select your project and instance and go to the Database Connections view.
- Click Connect to Source Database and ensure the Postgres tab is selected.
- Locate the connection details from AWS RDS:
- Copy the “Endpoint” value from the AWS Management Console.
- Paste the endpoint into the “Host” field in the PowerSync Dashboard.
- Complete the remaining fields: “Name”, “Host”, “Port”, “Database name”, “Username”, “Password” and “SSL Mode” are required. You can paste a connection string into the “URI” field to simplify this.
- “Name” can be any name for the connection.
- “Port” is 5432 for Postgres databases.
- “Username” and “Password” maps to the
powersync_rolecreated in Source Database Setup. - PowerSync has the AWS RDS CA certificate pre-configured —
verify-fullSSL mode can be used directly, without any additional configuration required.
- Click Test Connection and fix any errors.
- Click Save Connection.
Troubleshooting
If you get an error such as “IPs in this range are not supported”, the instance is likely not configured to be publicly accessible. A DNS lookup on the host should give a public IP, and not for example10.x.x.x or 172.31.x.x.Azure Postgres
Azure Postgres
- In the PowerSync Dashboard, select your project and instance and go to the Database Connections view.
- Click Connect to Source Database and ensure the Postgres tab is selected.
- Fill in your connection details from Azure.
- “Name”, “Host”, “Port”, “Database name”, “Username”, “Password” and “SSL Mode” are required. You can also paste a connection string into the “URI” field to simplify data entry.
- “Name” can be any name for the connection.
- “Port” is 5432 for Postgres databases.
- “Username” and “Password” maps to the
powersync_rolecreated in Source Database Setup. - PowerSync has the Azure CA certificate pre-configured —
verify-fullSSL mode can be used directly, without any additional configuration required.
- Click Test Connection and fix any errors.
- If you encounter the error
"must be superuser or replication role to start walsender", ensure that you’ve followed all the steps for enabling logical replication documented here.
- If you encounter the error
- Click Save Connection.
Google Cloud SQL
Google Cloud SQL
- In the PowerSync Dashboard, select your project and instance and go to the Database Connections view.
- Click Connect to Source Database and ensure the Postgres tab is selected.
- Fill in your connection details from Google Cloud SQL.
- “Name”, “Host”, “Port”, “Database name”, “Username”, “Password” and “SSL Mode” are required. You can paste a connection string into the “URI” field to simplify data entry.
- “Name” can be any name for the connection.
- “Port” is 5432 for Postgres databases.
- “Username” and “Password” maps to the
powersync_rolecreated in Source Database Setup. - The server certificate can be downloaded from Google Cloud SQL.
- If SSL is enforced, a client certificate and key must also be created on Google Cloud SQL, and configured on the PowerSync instance.
- Click Test Connection and fix any errors.
- Click Save Connection.
Neon
Neon
- In the PowerSync Dashboard, select your project and instance and go to the Database Connections view.
- Click Connect to Source Database and ensure the Postgres tab is selected.
- Fill in your connection details from Neon.
- “Name”, “Host”, “Port”, “Database name”, “Username”, “Password” and “SSL Mode” are required. You can paste a connection string into the “URI” field to simplify data entry.
- “Name” can be any name for the connection.
- “Port” is 5432 for Postgres databases.
- “Username” and “Password” maps to the
powersync_rolecreated in Source Database Setup. - Note that if you’re using a self-signed SSL certificate for your database server, click the Download Certificate button to dynamically fetch the recommended certificate directly from your server.
- Also note if you get any error such as
server certificate not trusted: SELF_SIGNED_CERT_IN_CHAIN, click Download Certificate to attempt automatic resolution.
- Click Test Connection and fix any errors.
- Click Save Connection.
Fly Postgres
Fly Postgres
- In the PowerSync Dashboard, select your project and instance and go to the Database Connections view.
- Click Connect to Source Database and ensure the Postgres tab is selected.
- Fill in your connection details from Fly Postgres.
- “Name”, “Host”, “Port”, “Database name”, “Username”, “Password” and “SSL Mode” are required. You can paste a connection string into the “URI” field to simplify data entry.
- “Name” can be any name for the connection.
- “Port” is 5432 for Postgres databases.
- “Username” and “Password” maps to the
powersync_rolecreated in Source Database Setup. - Note that if you’re using a self-signed SSL certificate for your database server, click the Download Certificate button to dynamically fetch the recommended certificate directly from your server.
- Also note if you get any error such as
server certificate not trusted: SELF_SIGNED_CERT_IN_CHAIN, click Download Certificate to attempt automatic resolution.
- Click Test Connection and fix any errors.
- Click Save Connection.
PlanetScale
PlanetScale
- In the PowerSync Dashboard, select your project and instance and go to the Database Connections view.
- Click Connect to Source Database and ensure the Postgres tab is selected.
- Head to your PlanetScale database dashboard page at
https://app.planetscale.com/<ORGANIZATION>/<DATABASE_NAME>and click on the “Connect” button to get your database connection parameters.- In the PowerSync Dashboard, “Name”, “Host”, “Port”, “Database name”, “Username” and “Password” are required.
- “Name” can be any name for the connection.
- “Host” is the
hostconnection parameter for your database. - “Port” is 5432 for Postgres databases.
- “Username” and “Password” maps to the
powersync_rolecreated in Source Database Setup.- Important: PlanetScale requires your branch ID to be appended to your username. The username should be
powersync_role.<branch_id>. Your PlanetScale branch ID can be found on the same connection details page.
- Important: PlanetScale requires your branch ID to be appended to your username. The username should be
- SSL Mode can remain the default
verify-full.
- Click Test Connection and fix any errors.
- Click Save Connection.
Other / Self-hosted
Other / Self-hosted
- In the PowerSync Dashboard, select your project and instance and go to the Database Connections view.
- Click Connect to Source Database and ensure the Postgres tab is selected.
- Fill in your connection details.
- “Name”, “Host”, “Port”, “Database name”, “Username”, “Password” and “SSL Mode” are required. You can paste a connection string into the “URI” field to simplify data entry.
- “Name” can be any name for the connection.
- “Port” is 5432 for Postgres databases.
- “Username” and “Password” maps to the
powersync_rolecreated in Source Database Setup. - Note that if you’re using a self-signed SSL certificate for your database server, click the Download Certificate button to dynamically fetch the recommended certificate directly from your server.
- Also note if you get any error such as
server certificate not trusted: SELF_SIGNED_CERT_IN_CHAIN, click Download Certificate to attempt automatic resolution. - Click Test Connection and fix any errors.
- Click Save Connection.
Make sure that your Postgres database allows access to PowerSync’s IPs — see Security and IP Filtering
- Postgres Source Database Setup
- Security & IP Filtering: TLS with Postgres
MongoDB Specifics
- In the PowerSync Dashboard, select your project and instance and go to Database Connections.
- Click Connect to Source Database and ensure the MongoDB tab is selected.
- Fill in your connection details from MongoDB:
- Copy your cluster’s connection string from MongoDB and paste it into the URI field in the PowerSync Dashboard. PowerSync will automatically parse this URI to populate other connection details.
- The format should be
mongodb+srv://[username:password@]host/[database]. For example,mongodb+srv://admin:<db_password>@cluster0.abcde1.mongodb.net/powersync
- The format should be
- Enter your database user’s password into the Password field. See the necessary permissions in Source Database Setup.
- “Database name” is the database in your cluster to replicate.
- Copy your cluster’s connection string from MongoDB and paste it into the URI field in the PowerSync Dashboard. PowerSync will automatically parse this URI to populate other connection details.
- Click Test Connection and fix any errors. If have any issues connecting, reach out to our support engineers on our Discord server or otherwise contact us.
- Click Save Connection.
Make sure that your MongoDB database allows access to PowerSync’s IPs — see Security and IP Filtering
MySQL (Beta) Specifics
Select your MySQL hosting provider for steps to connect your newly-created PowerSync instance to your MySQL database:AWS Aurora
AWS Aurora
To enable binary logging and GTID replication in AWS Aurora, you need to create a DB Parameter Group
and configure it with the necessary parameters. Follow these steps:
-
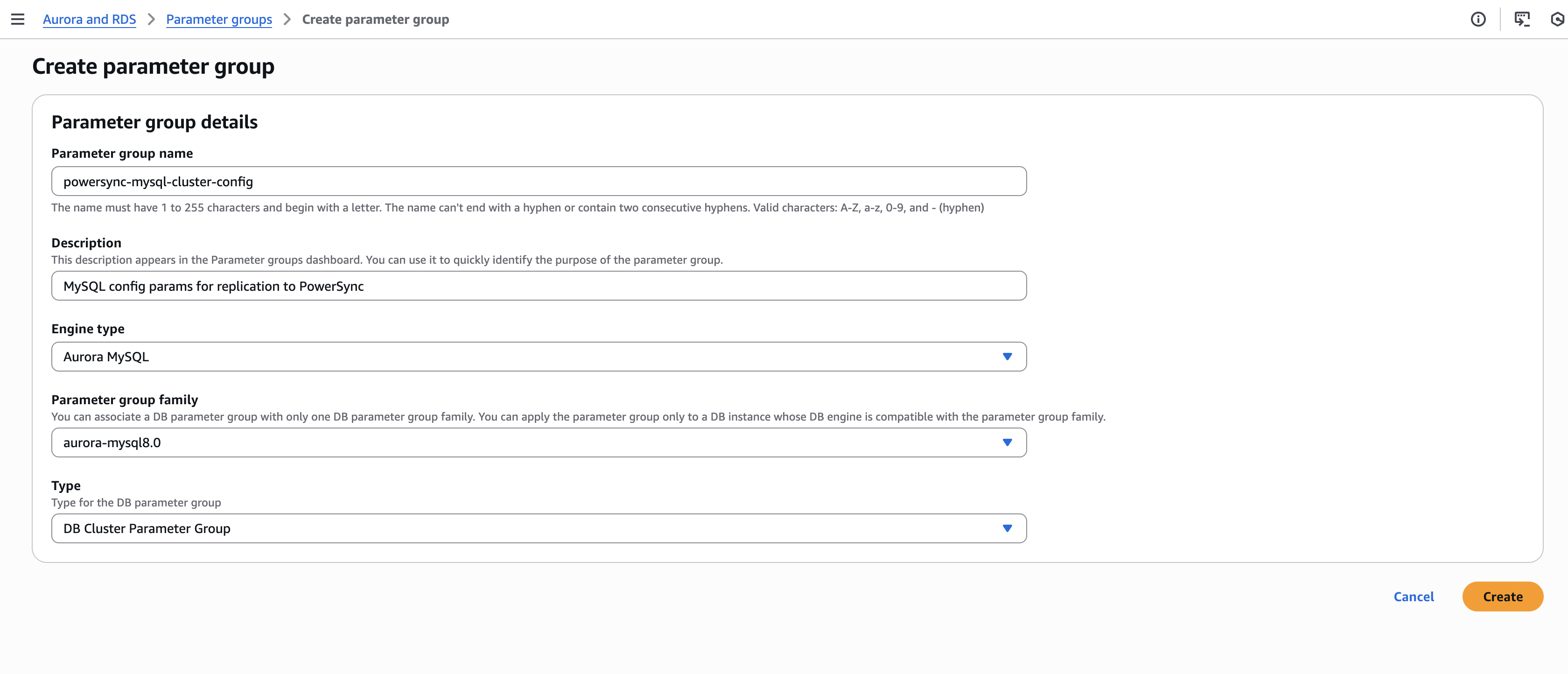
Navigate to Amazon RDS console
In the navigation pane, choose Parameter groups and click on Create Parameter Group:
-
Add all the required binlog configuration parameters. For example:
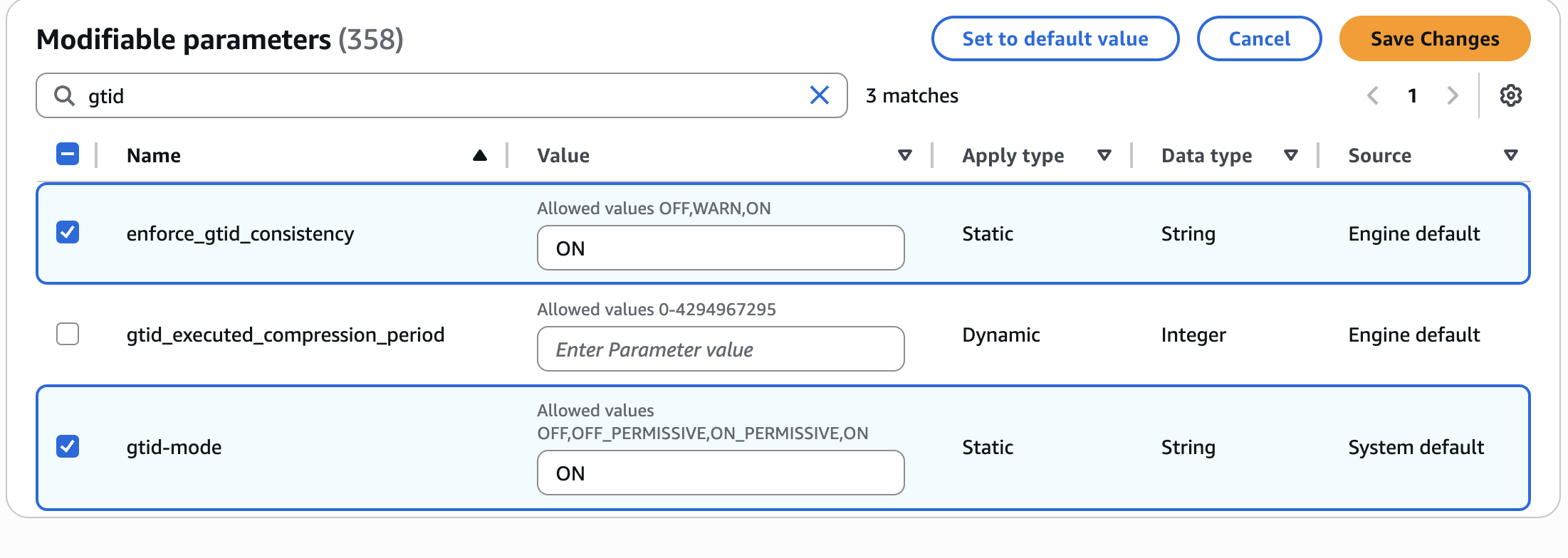
-
Associate your newly created parameter group with your Aurora cluster:
- In the navigation pane, choose Databases.
- Select your Aurora cluster.
- Choose Modify.
- In the DB Parameter Group section, select the parameter group you created.
- Click Continue and then Apply immediately.
- Whitelist PowerSync’s IPs in your Aurora cluster’s security group to allow access. See Security and IP Filtering for more details.
- In the PowerSync Dashboard, select your project and instance and go to the Database Connections view.
- Click Connect to Source Database and ensure the MySQL tab is selected.
-
Fill in your MySQL connection details from AWS Aurora:
- “Name”, “Host”, “Port”, “Database name”, “Username”, “Password” are required.
- “Name” can be any name for the connection.
- “Host” is the endpoint for your Aurora cluster.
- “Database name” is the default database to replicate.
- “Username” and “Password” maps to your database user.
- Click Test Connection and fix any errors.
- Click Save Connection.
Other / Self-hosted
Other / Self-hosted
- In the PowerSync Dashboard, select your project and instance and go to the Database Connections view.
- Click Connect to Source Database and ensure the MySQL tab is selected.
-
Fill in your MySQL connection details:
- “Name”, “Host”, “Port”, “Database name”, “Username”, “Password” are required.
- “Name” can be any name for the connection.
- “Host” the endpoint for your database.
- “Database name” is the default database to replicate. Additional databases are derived by qualifying the tables in the Sync Rules.
- “Username” and “Password” maps to your database user.
- Click Test Connection and fix any errors.
- Click Save Connection. PowerSync deploys and configures an isolated cloud environment for you, which can take a few minutes to complete.
Make sure that your MySQL database allows access to PowerSync’s IPs — see Security and IP Filtering
SQL Server (Alpha) Specifics
SQL Server support was introduced in version 1.18.1 of the PowerSync Service.
- In the PowerSync Dashboard, select your project and instance and go to the Database Connections view.
- Click Connect to Source Database and ensure the “SQL Server” tab is selected.
- Fill in your SQL Server connection details:
- “Name”, “Host”, “Port”, “Database name”, “Username”, “Password” are required.
- “Name” can be any name for the connection.
- “Host” is the endpoint for your SQL Server instance.
- “Port” is typically 1433 for SQL Server (default port).
- “Database name” is the database where CDC is enabled.
- “Username” and “Password” maps to the database user created in Source Database Setup (e.g.,
powersync_user).
- Click Test Connection and fix any errors.
- Click Save Connection.
Make sure that your SQL Server database allows access to PowerSync’s IPs — see Security and IP Filtering